CRM User Access Controls
16 Jan 2023
(Republished from an earlier article)
A few months back, we added some new features that allow you to control how your users access your CRM system. These various user access controls give you, as a system administrator, the ability to add an extra layer of security (on top of what we already do).
But first…
What are User Access Controls?
User Access Controls are features within a piece of software, like a CRM system, that let you decide how your users login into your system.
For example, these kinds of controls can help you ensure your users are always:
- Viewing only the data they have permission to see,
- Logging in from a secure location,
- Using a strong password,
- Going through additional authentication, and
- Protecting your data when they leave their desk.
In OpenCRM, that first option is covered by our (extensive) permission controls. (You can read more about exactly how to set these up in this Knowledgebase article.) But it’s the other four (plus a few extras) that I’d like to discuss in this blog.

Do we have what it takes?
We don't restrict which features you have access to in OpenCRM based on how many users you have. You get everything right out of the box. Click to find out if we've got the features you need.
find out moreSession timeouts
The first user access control feature I’d like to discuss was introduced in one of our 2021 batch of updates. It allows you to set what is known as a session timeout.
Session timeouts are when your users are automatically logged out after a period of inactivity.
Let’s say, for example, that you set your session timeout to be one hour. This would mean that, when one of your users leaves their desk for lunch (let’s say 30 minutes) and then gets caught up in a meeting (plus 45 minutes), they will need to log back into OpenCRM when they get back to their desk.
But don’t worry, they won’t lose any unsaved data on screen. They’ll just see a popup like this:

Where they can re-enter their username/password and then get stuck right back into their work. And as with the vast majority of OpenCRM, the specific session timeout length can be dictated by you and what works best for your company.
Multi-Factor Authentication (MFA)
So that covers your users after they’ve already logged into your CRM system, but what about while they’re logging in?
In recent years, the ever-popular feature known as Multi-Factor Authentication has swept across the world of user access controls (and for very good reason). This feature forces your users to include a code from a secondary application to their login details.
This secondary application is often accessed from a mobile (or sometimes a browser extension). It relies on the logic that, if your user is really who they say they are, then they will have their mobile phone within easy reach.
You’ll have probably used this before with your internet banking or social media. In practice, your users will enter their username and password, then generate a code on their mobile, enter it into OpenCRM, and boom. They’re logged in securely. And you know that when ‘Gary’ logs in, it is indeed Gary gaining access to your CRM system.
Given the fact that as many as 59% of people use the same password for multiple systems. That extra bit of authentication can add a much-needed layer of security to your users’ logins.
Watch and learn
If you're looking for further information on how specific features and functionality play out in OpenCRM, why not click to check out our webinars?
watch nowPassword Policy
Another set of controls you have over how your users access your CRM system is around the step before MFA: the all-important password.
In OpenCRM you can set up a password policy, effectively requiring your users to follow certain rules when setting up their password. These controls include:
- Setting how long the password has to be,
- Forcing them to use mixed cases (ExampLe vs example),
- Requiring numbers to be included (example5 vs example),
- Making your users include symbols (exam#ple vs example), and
- Not allowing them to use dictionary words (Y78skje vs Password)
There are lots of tips out there on how you can build a strong password, this feature just forces your users to follow some of the key advice.
Additionally, you can set a maximum number of login attempts your users can make before their user is locked. This means that someone can only try an incorrect password so many times before they are locked out and have to reset that password. This protects your system from what is known as brute force attacks—where someone tries to login to a system by essentially trying lots and lots of different variations of a password.
IP Locking
Even before your users start entering passwords or MFA codes, you have yet another access control in your arsenal. And it has to do with IP addresses.
You actually have quite a few options here (set up instructions), but I’ll start with the basics.
Every time you connect to the internet, whether it’s over wifi, 5G, ethernet, etc, you will have an IP address. Think of it like sending and delivering post. Your postie (in this example your Internet Service Provider) knows where to deliver your post because it has your home address on it. Anyone you send a letter to knows who it comes from because it has your address on it as the sender.
Your IP Address works the same way, it sends your requests out via your IP address. And then sends information back to you via this same address. That address is unique to your connection at that time. It’s more complicated than that (here’s more information if you’re interested), but that’s the basics.
This means that you can control access to your CRM system based on the IP address of the user logging in.
You can choose to either allow traffic from only authorised IP addresses (maybe your office and VPN only) or ban traffic from certain IP addresses (a known threat).
If someone tries to access your system from a banned IP address, they will be redirected to a page of your choosing. If one of your users tries to access the system from an unauthorised IP address, on the other hand, they will be notified and told how to request authorisation.
But remember, any IP address restrictions you add will also be implemented on the mobile app.

Don't just take our word for it
Click to read how other companies have benefited from using OpenCRM. From out-of-the-box implementations to businesses that needed bespoke development to fit their unique approach - we've seen it all.
find out moreExtra User Access Controls
In addition to the above user access controls, we have a couple of other features that can help you oversee your users. The goal here isn’t to turn you into ‘Big Brother’ or make your team feel like you’re spying on them.
The goal is to give you the tools you need to protect your company data.
Audit Login History
To start off, you may or may not be aware of our Audit Log functionality. It allows you to view who has looked at a record, edited it, and even record what changes they made.
We have a similar feature directly within the user management area of the settings. It is accessed via the Login History button, which is available on the main User page or an individual User.
Clicking this button will display when someone logged in and out. It will also show when someone has tried to login and failed to do so.
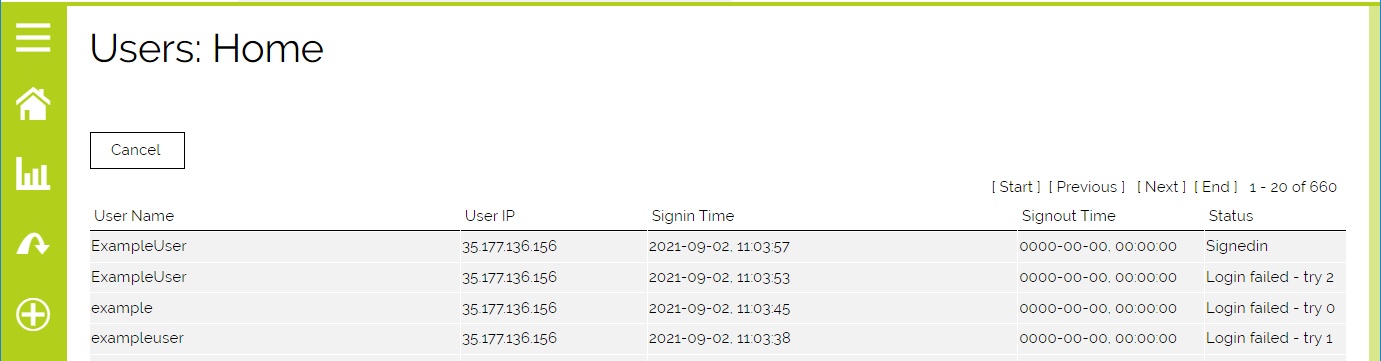
As you can see, this is a great way to view not only the basic login information, but also a way to help someone who is trying to login with the wrong username. While not an access control, exactly, it is just one more tool in your user management toolbox.
Managing your Users
When it comes to more general user management, of course, we have the basics covered.
Adding new users and editing existing ones is as easy as creating or editing a Lead or Contact. Although there might be more you need to consider from a user permission / access point of view, the actual mechanisms of this are very straightforward.
Occasionally, of course, you will also have to remove someone’s access to your CRM system. And here again, we give you a few options.
You can make a user Inactive (or Lock them out) and stop them logging in. You could also Delete the user, which has the same effect when it comes to their ability to login. The difference is down to what happens to the records assigned to that user.
But either way, the control is in your hands.
Let us take you on a tour
You've had a look around and are starting to think OpenCRM might be the system for you and your business. Why not chat with one of our team (and ask your burning CRM questions) as they take you on a tour of the system?
find out moreI hope this blog has helped you understand the myriad of options you have in OpenCRM. If you’d like to chat through any of these options, why not click the icon on the right and start chatting?
Before I got my start in the tech industry as part of Apple’s UK Mac launch team, I was a professional drummer (notice I didn’t say musician). But once I got in, I was hooked and I’ve been involved in the tech industry, primarily software development, for over 35 years. I founded this company and I now have the enviable title of System Architect (as well as Managing Director) here at OpenCRM.